User group manages permission assignment across dashboard users in your organization. Create a user group for each department, job function, region, franchisee, or any other dimension that fits your organizational hierarchy. Permissions are assigned at the group level. When a user is added to multiple groups, they receive the collective set of permissions from all the groups that they have membership.
To set up user groups in your organization, start from the organization settings page (as shown below).
If you plan to use custom data in your access strategy, please create the needed custom properties before setting up user groups. See more details in the custom permission data guide.
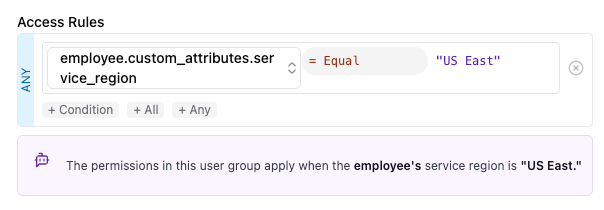
When creating a new group, first select a set of users to join the group. Then configure the access rule. For example, a customer may have an organization divided into multiple service regions. To limit access by service region, they would first create a custom property representing the service region that each employee belongs to. They can then create a user group to represent, for example, "US East Onboarding Admins". To limit all the permissions assigned to this group to the "US East" service region, they can configure the group access rule as shown below:
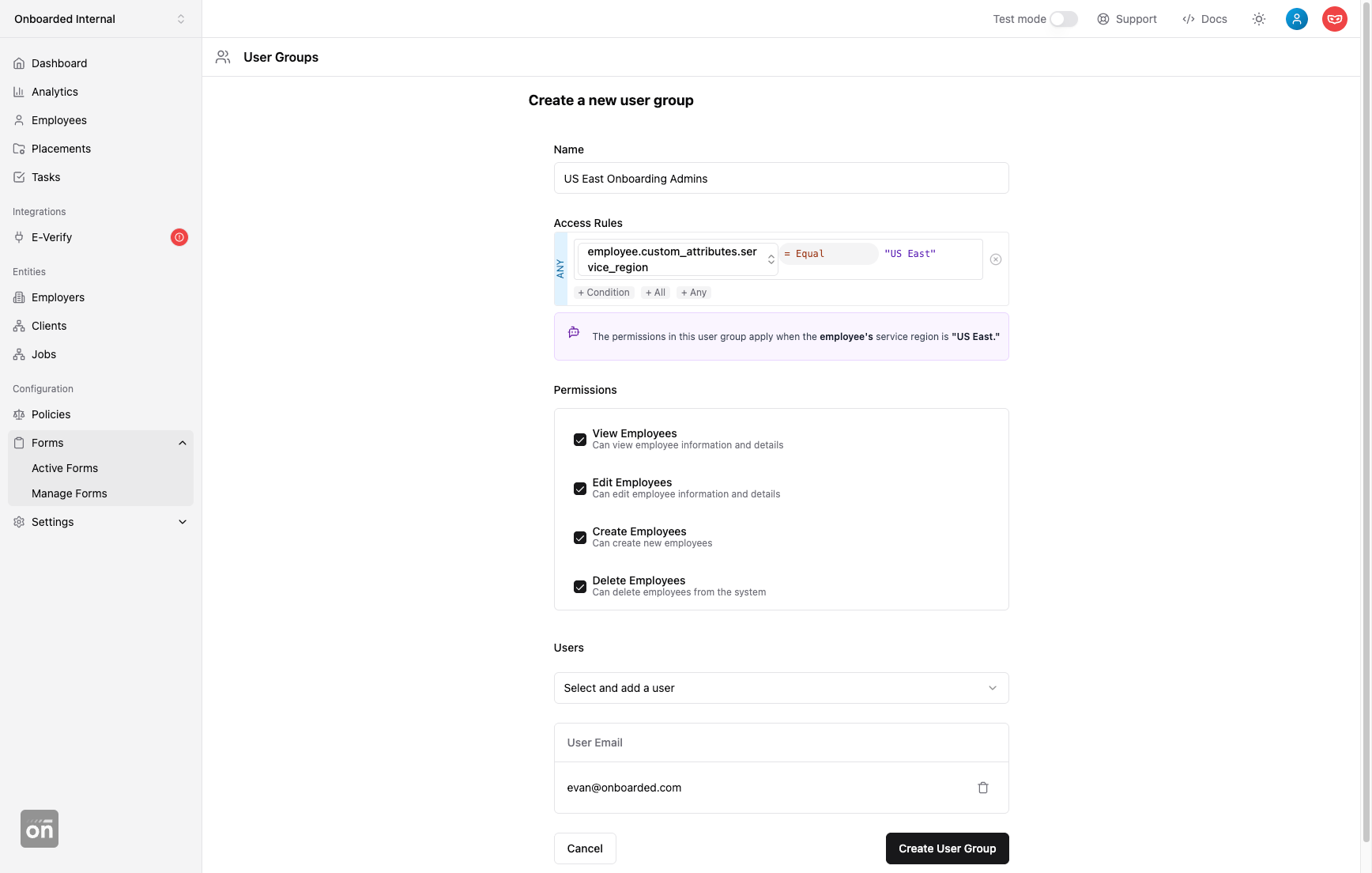
After that, select all the permissions that users in this group should receive. For example, the screenshot below creates a user group that gives its users full access to manage employees in the "US East" service region (based on employee custom attributes).
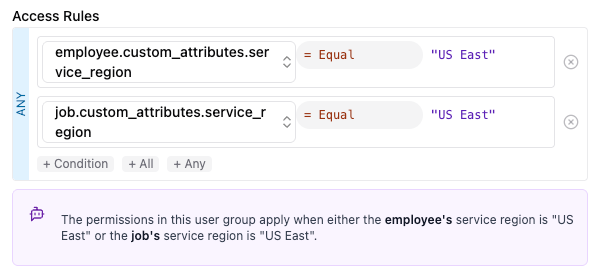
You can create a user group with permissions of different entities. For example, you can assign both employee:view and employer:view permissions under the same group. It is important, however, that the access rule is configured with the following considerations (as shown in screenshot below):
- The rule must have a top-level
ANYcondition. - Each entity type (employee, employer, etc.) must have its own condition in the rule.
When visiting a record in the system (such as an employee), Onboarded applies the record's properties against the dashboard user's permissions and their associated access rule. Access is granted only when both of the following conditions are met:
- User has the needed permission (such as
employee:read). - The access rule associated with that permission is evaluated successfully as a whole against the record's properties. For example, if the access rule requires
service_regionto be "US East", access will only be granted for employees with that custom attribute.
If you were to, for example, grant a job:view permission without a corresponding job-based condition in the access rule, the job permission will never grant access to any jobs. In summary, permissions determine the actions that a group of users is allowed to perform; whereas access rules determine the context or scope under which those actions can be performed.
For complex use cases, we recommend keeping each user group specific to one entity. For example, you may create one user group to manage employee access for each region; another to manage employer access etc. This keeps the access rule simple and readable and lowers the risk of misconfiguration.
Next, continue reading to learn more about data view.